Part 1 of this blog series discussed how users and enterprises that delayed the implementation of a previously discovered vulnerability in the Windows operating system became victims of the WannaCry ransomware. Since all organizations with industrial control systems (ICS) run the devices from Windows endpoints, they are potential targets of ransomware. With the difficulty involved in supervisory control and data acquisition (SCADA) connectivity, once a company has the system working properly, it usually issues a policy stating that the PCs used for the connectivity shall not ever be updated. As a result, by corporate mandate, the most important PCs in the company are also the most vulnerable to attack by something like WannaCry or other ransomware.
However, for security in ICS applications, the International Society of Automation (ISA) and North American Electric Reliability Committee (NERC) developed the ISA 99 and NERC Critical Infrastructure Protection (CIP) standards. These standards define how to build a secure network to protect devices that have no ability to protect themselves. Technology from the Trusted Computing Group (TCG) is an enabler of ISA99 and NERC CIP compliance.
With TCG’s Trusted Platform Module Trusted Platform Module (TPM) and Trusted Network Communications (TNC) specifications, users have a network security architecture, where credential authentication ensures authorized physical access from inside and outside of the network and data across the network and in the cloud is protected.
While TCG standards do not directly provide protection against ransomware, there is an indirect approach. To obtain the desired protection, users have to isolate ICS devices and high value, unsecurable PCs used to control them on a virtual network. This means that the high value PCs cannot be allowed to directly connect to any Windows platform that has a network connection outside of the protected group. Instead, an indirect connection is required to outside networks, perhaps through a Linux-based machine.
Beyond the ICS portion of an organization, TCG standards address establishing trust throughout any enterprise’s network from bring your own device (BYOD), cloud computing, data in transit, data at rest and all the other vulnerabilities.
Preventing Future Ransomware Efforts from Impacting an Entire Enterprise’s Network
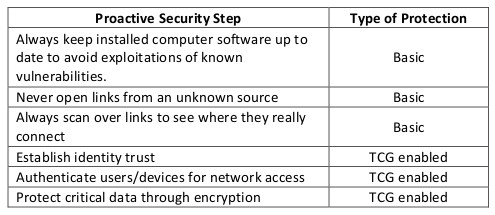
There are a few basic steps that need to be reinforced through training and messaging and a few advanced TCG standards enabled steps that should be implemented to protect enterprise computers and the network. Table 1 summarizes these steps.
Table 1: Steps to Take to Prevent Problems/Exploits in Your Organization

Good Morning
With the disruptive, very costly and potentially even deadly impact of computer hackers on an enterprise’s ICS computers and networks, these high value targets must take full advantages of the security, trust and protective tools that are available. The experts in various TCG committees have pooled their expertise to establish trust in IoT connections to computers, smart devices, networks, storage devices and more – essentially any digital technique that could be used to compromise an entity’s property and brand. It’s time to head the wake-up call from the most recent digital disaster and implement this trust in your organization’s potentially vulnerable assets to prevent the rest of the day, and many subsequent days, from being ruined.