The increasing use of mobile devices or the integration of remote embedded systems introduces new threats to enterprise IT networks. While most security programs such as desktop firewalls, antivirus and hard drive encryption work pretty well for laptops, they are not available for mobile devices or remote VPN devices connecting to a central network.
The only way to keep the network secure is by providing additional security on the central IT infrastructure and establishing trust in the devices used.
The problem is, most of today’s security systems work isolated from each other and if they offer interoperability they do so only to a limited extent, which is insufficient to counter the new threats network security faces every day. TNC IF-MAP provides the possibility to interconnect different IT-security systems and provide an accurate representation of the health status of an IT network. The TPM offers the perfect solution for establishing trust in a remote device by checking its health during boot-up.
At last month’s RSA Conference, TCG member NCP of Germany demonstrated the integration of different IT security systems like firewalls, intrusion detection and VPN working together in real time to counter threats emerging from a remote device or a smartphone. If the device should misbehave within the internal network this is detected and the device is limited in its access or shut off the network.

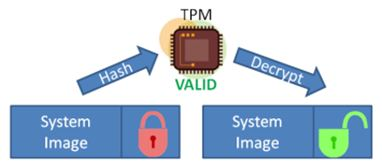
In the case of a remote embedded device the device additionally checks its health during bootup using the TPM and only establishes connection if the device image is correct.


For more information about TCG and its RSA seminar event, which included this demo and others as well as panel sessions, go to RSA 2013 – Trusted Computing: Billions of Secure Endpoints in 10 Years